Introduction
We want to do some malware analysis, but to do so, we need a lab that will server the following functions:
- Not infect our host.
- Proxy the guest network traffic in order to:
- Inspect it.
- Manipulate it.
- Block it.
For the host isolation we need a hypervisor. You can use either a type 1, like KVM, ESXi or Hyper-V or a type 2 hypervisor, like VirtualBox or VMware Workstation. To keep it simple and OS-agnostic we will use VirtualBox.
Virtual Machine
Download Windows
You can download a free evaluation Windows VM image from Microsoft valid for 90 days. The 90 days expiration is not a problem for as because we will take a snapshot and roll it back when it does expire. Select MSEdge on Win10 (x64) Stable 1809 and the hypervisor you want to use, in my case VirtualBox.
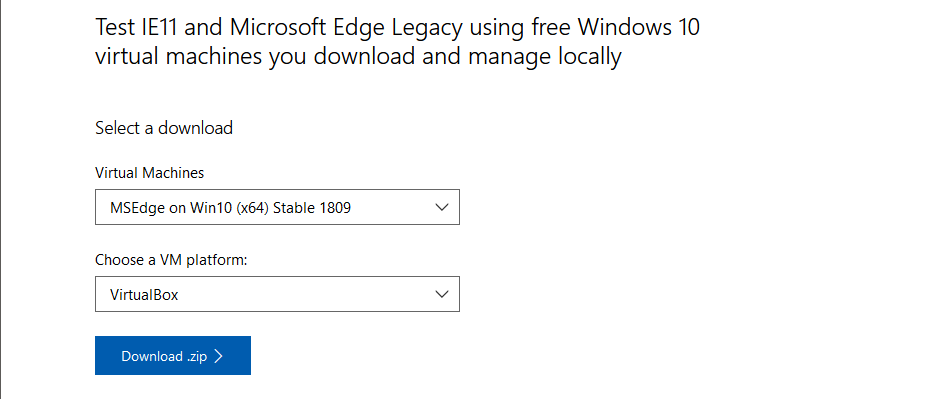 Download a free Windows VM from Microsoft
Download a free Windows VM from Microsoft
When downloaded and imported to VirtualBox and change the CPUs and the memory to your liking. I will go with 4 CPUs and 8 GB of RAM. I also recommend that you change the Display > Video Memory to more than 16 MB.
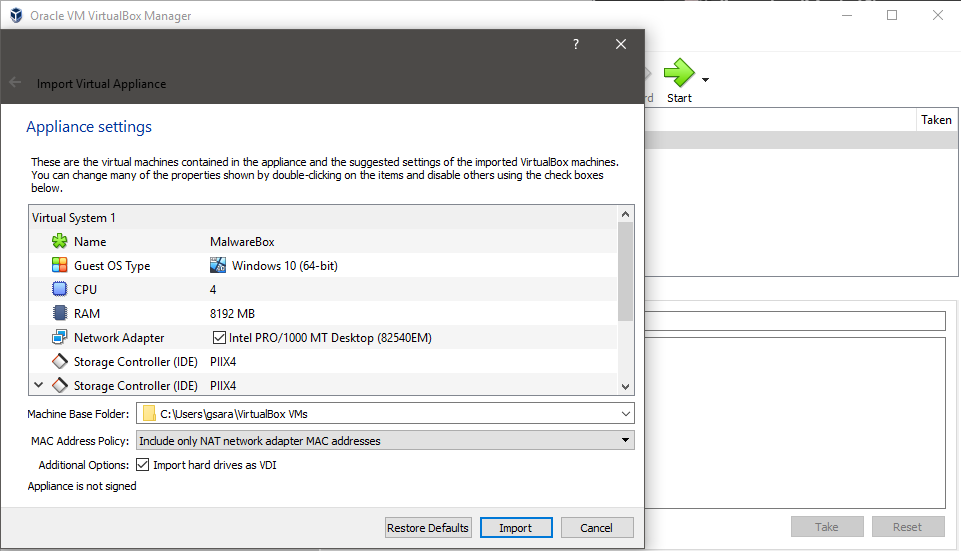 Importing the OVA to VirtualBox
Importing the OVA to VirtualBox
When imported, take a snapshot so you can roll back to this state.
The VM’s username is IEUser and the password is Passw0rd!
Customized Flare VM
Next we will install some software to make our analysis easier. We will install some of the packages from Flare VM which is a malware analysis, incident response, penetration testing, etc. distribution from FireEye. The problem is that it requires up to 50GB of storage and in most cases we will only use a subset of the installed packages, so we will install only the ones that we need.
Customization
We need to download and install the Flare VM repository and extract it. Now open the profile.json file and modify the packages list to the ones that you would like to install referring to packages.csv. The ones that I picked are here. If you want to install some of the additional ones you just have to open a Powershell as an administrator and execute the How to install line of the package that you want to install from packages.csv.
Installation
Now we need to open a Powershell terminal as an administrator and navigate to the repository. Then set the execution policy to unrestricted and execute the install.ps1 script with the customized profile.json and the password of the VM as arguments.
1
2
Set-ExecutionPolicy unrestricted
.\install.ps1 -profile_file profile.json -password 'Passw0rd!'
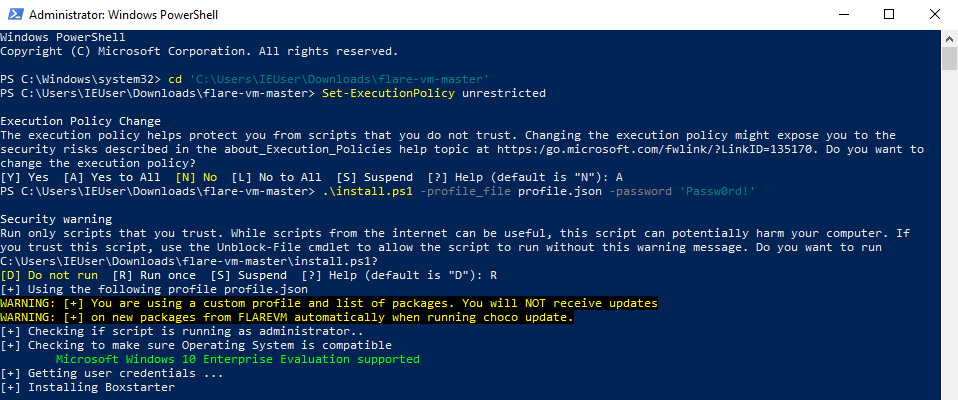 Installing the customized Flare VM packages
Installing the customized Flare VM packages
You may get an error while disabling the Windows Defender Service. 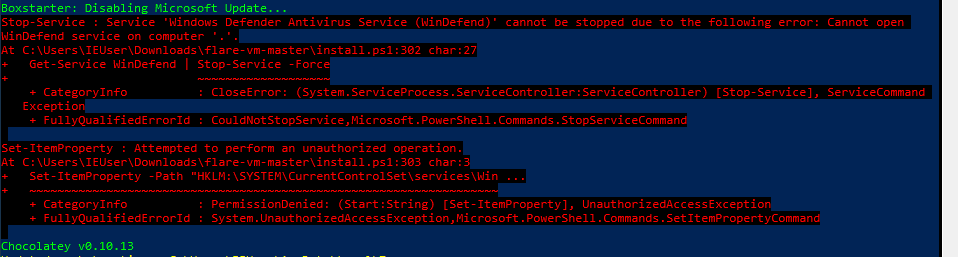 Windows Defender Service disabling error
Windows Defender Service disabling error
If you do Ctrl+C the script, and disable it manually by running the following command on the administrator powershell session:
1
Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend
Then restart the VM and re-run the Flare VM installation script.
Be patient, it will take a long time to finish.
Update Windows Defender
Update-MpSignature
Once it’s finished, take another snapshot so you can revert it back if the licence expires or the VM becomes infected.
Proxy
Linux VM Installation
Now we need to create a proxy that will inspect all the traffic from our VM to the internet. This will be on Linux Virtual machine in the same or other hypervisor, or in the cloud. If you want to use Linode, you can get $200 free credit for 2 months using my referral code.
Choose whatever distro you like, I will go with Alpine. I will assume that you chose Alpine also, if not adjust the procedure accordingly.
Alpine Installation
For the VM, I recommend 1 CPU, 256 MB of RAM and 8 GB of storage.
 Creating the Proxy VM
Creating the Proxy VM
Mount the downloaded ISO file and start the VM. Login as root and install Alpine:
1
setup-alpine
Follow the installation instructions and keep the defaults except from when it asks you Which disk(s) would you like to use?, then type ? set the disk name as required, set the volume as lvm, then sys and continue to erase the disk as seen bellow.
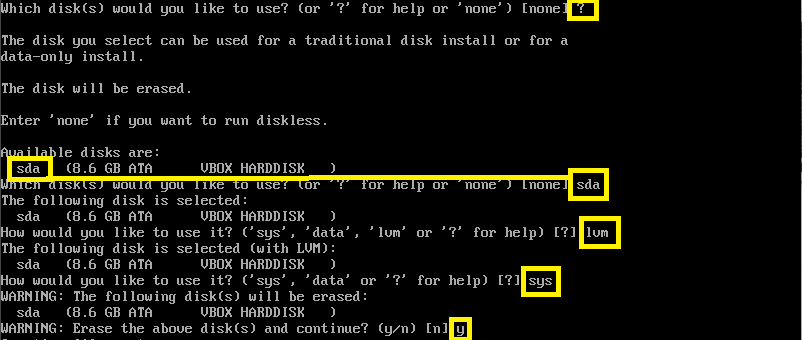 Alpine installation
Alpine installation
After the installation shut down the VM, remove the mounted ISO and start it again. The user is root and the password the one that you chose during the installation.
Squid Installation
Now we need to install a proxy, I will go with Squid.
Install the Squid proxy, add it to startup and start it:
1
2
3
apk add squid
rc-update add squid
rc-service squid start
To make sure that the proxy is working:
1
netstat -tl | grep 3128
 Making sure that Squid is working
Making sure that Squid is working
Network Configuration
Now we need to configure our malware analysis box to connect to the internet through the squid proxy. To do that we will create a new virtual network.
VirtualBox configuration
After the creation, we need shut down our VMs and perform the following:
Switch our Windows VM to the newly created NatNetwork. To do this, select the Windows VM and go to
Settings > Networkand on theAdapter 1tab switch adapter to theInternal Networkand name it as you want your new network to be called. Changing the Windows VM adapter settings
Changing the Windows VM adapter settingsCreate a new network adapter on the Alpine VM that connects to NatNetwork. To do this, select the Linux VM and go to
Settings > Network. OnAdapter 1tab leave the adapter asNATand on theAdapter 2tab enable the adapter and switch it to theInternal Networknamed as your newly created virtual network. Changing the Linux VM adapter settings
Changing the Linux VM adapter settings
Linux VM interface configuration
Time to boot both VMs again.
We need to set the correct IP on the second interface on the Linux VM. We need to find out the VLAN of the default gateway eth0:
1
ip addr
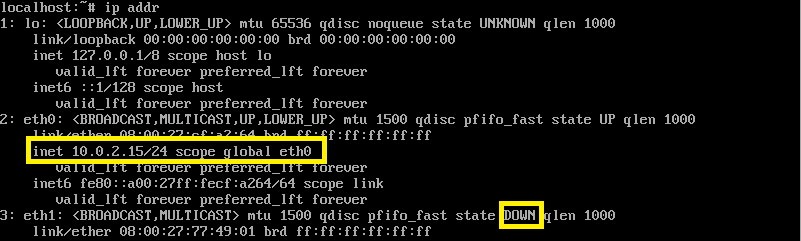 Checking connectivity towards the virtual switch that is NATed to the host network
Checking connectivity towards the virtual switch that is NATed to the host network
For me the default gateway is on the 10.0.2.0/24 subnet, so I will choose the 10.25.2.0/24 subnet for the internal communication. Let’s bring up the second interface with a new IP in the new subnet, I will choose 10.25.2.168:
1
2
ifconfig eth0 10.25.2.168 netmask 255.255.255.0 up
ip addr
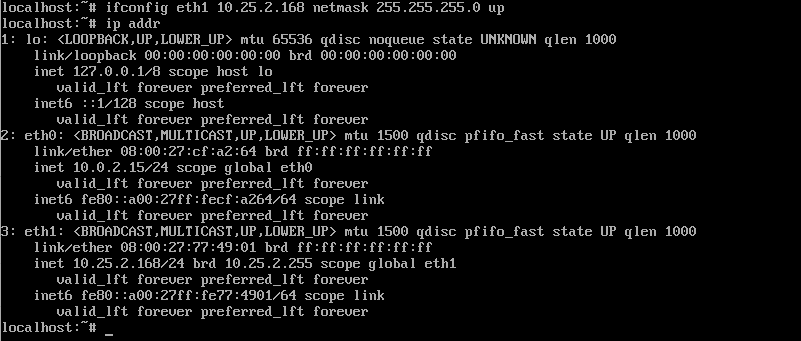 Changing the internal interface IP and bringing it up
Changing the internal interface IP and bringing it up
Windows VM interface configuration
Now we need to reconfigure the windows interface and proxy. On the Windows VM, go to Settings > Network & Internet > Ethernet > Change adapter options and got ot the properties of the ethernet interface. Then change the IPv4 address to one that is in the subnet that you chose. For me it’s going to be 10.25.2.2. There is no need to set default gateway or DNS as we only need to communicate with the proxy on 10.25.2.168. 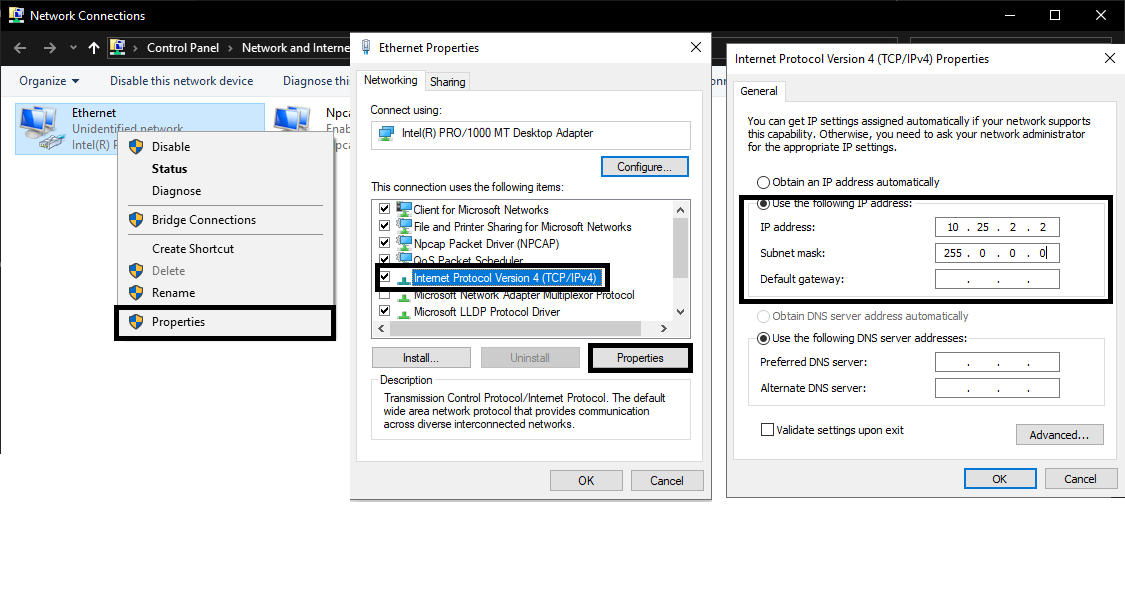 Changing the WIndows VM adapter settings
Changing the WIndows VM adapter settings
To confirm that we have successfully changed the interface to the one that the virtual switch is on, ping Linux VM: 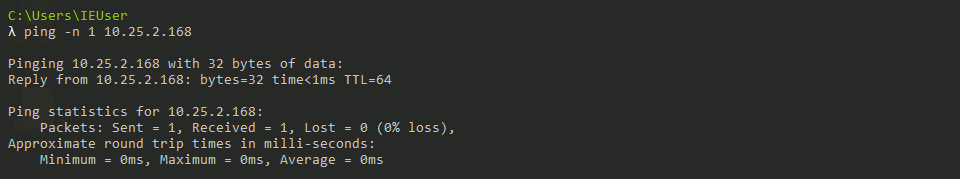 Checking connectivity towards the proxy
Checking connectivity towards the proxy
Now the only thing left is to change the proxy settings on the Windows VM. Go to Proxy Settings and put your Linux’s VM IP and 3128 as the proxy port. 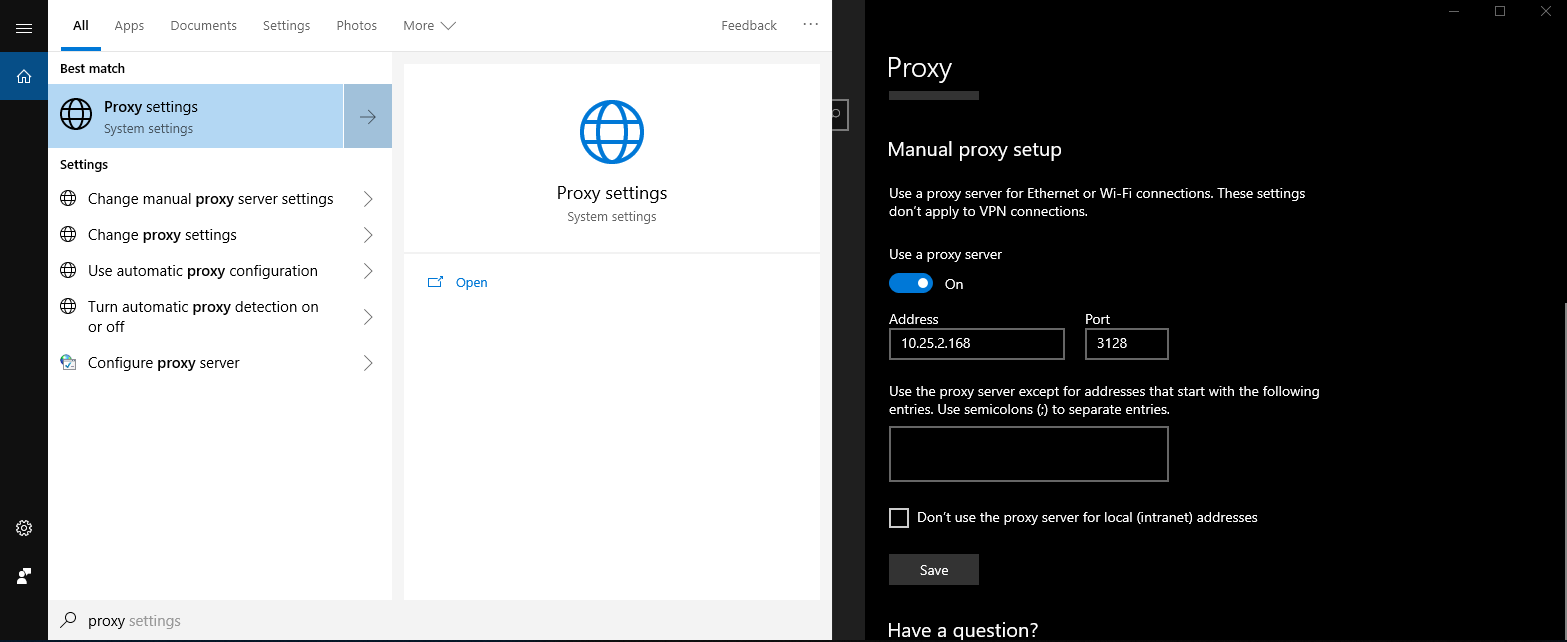 Checking connectivity towards the proxy
Checking connectivity towards the proxy
Conclusion
This is it! Now you have a malware analysis lab that is separated from your host network, and you can monitor/manipulate it’s traffic!
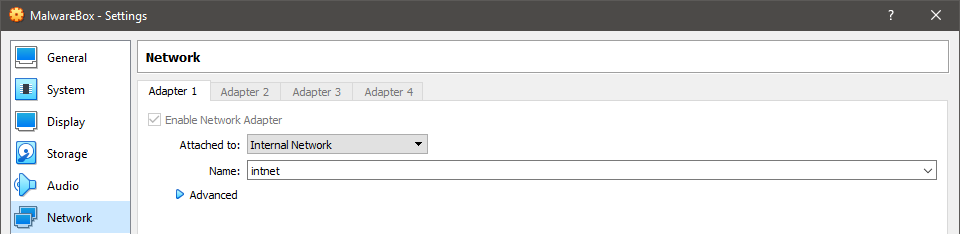 Changing the Windows VM adapter settings
Changing the Windows VM adapter settings